Today, we talk about 6 FAQs about the LoRa Encryption security mechanisms.
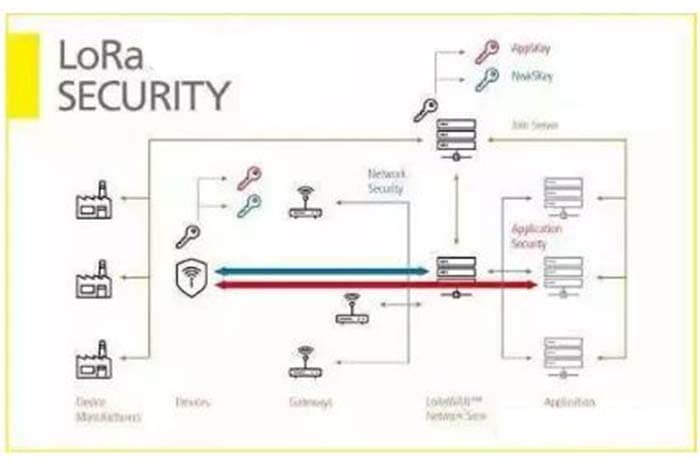
LoRa Encryption FAQ 1, where are the security mechanisms for LoRaWAN specified?
All security mechanisms are specified in the LoRa Alliance specification, which can be downloaded by the public.
LoRa Encryption FAQ 2, how does the LoRa Alliance specification ensure the secure operation of LoRaWAN networks?
LoRaWAN supports source authentication, full Media Access Control (MAC) integrity, and replays protection frameworks. This also enables end-to-end encryption of the application load between the end device and its components on the network side. LoRaWAN supports the operation of MAC command encryption modes allowed.
All these procedures rely on the Advanced Encryption Standard (AES), using 128-bit keys and algorithms.
LoRa Encryption FAQ 3, are there any differences in HQ (activation of personalization) and OTAA (over-the-air activation) methods in terms of security?
LoRaWAN uses both static and dynamic generation of the root key for the session key.
The root key is only in the configuration of the OTAA end device. They are used to derive the session key when the OTAA end device performs the connection process to the network.
An OTAA end device, when installed in the field, will be able to connect to any network that has an interface to the key server (i.e. join 1.1 publish server) that the end device is associated with. The session key is passed through the end device and is used to protect the traffic in the air.
ABP end devices do not provide the root key. Instead, they provide a set of session keys for the pre-selected network. The session keys remain unchanged throughout the life of the ABP end device.
The ability of OTAA devices to update session keys is better suited for applications that require a higher level of security.
LoRa Encryption FAQ 4, what kind of identification is used in LoRaWAN?
Each end device is identified by a 64-bit globally unique extended unique identifier.
The identifier (EU-64), is assigned by the manufacturer or the owner of the end device. The assignment of the EUI64 identifier requires the assignor to have an Organizational Unique Identifier (OUI) from an IEEE registry.
Each connected server used to authenticate an end device is also identified by a 64-bit globally unique identifier (EU-64) assigned by the owner or operator of that server.
Open LoRaWAN networks and private LoRaWAN networks cooperate (roaming) with the open network identified by a 24-bit globally unique identifier of the assigned resource federation.
When an end device successfully joins the network, it gets a 32-bit ephemeral device address assigned by the serving network.
LoRa Encryption FAQ 5, can I assign any identifier to my device or network at will?
Please see the previous question about assigning authority to each identifier. Not following these guidelines will cause your network to deploy identifier conflicts and unpredictable behavior (similar to what happens when connecting to the same LAN using multiple devices with the same Ethernet MAC address).
LoRa Encryption FAQ 6, are all end devices equipped with the same "default" device? When the key leaves the manufacturer?
No, there is no concept of “default key” or “default password” in LoRaWAN. All end devices are equipped with a unique key when they leave the manufacturer. Therefore, any compromise of a key from one end device will not affect other end devices.
Besides the 6 FAQs About The LoRa Encryption article, you may also be interested in the below articles.
What is the difference between WIFI and WLAN?
Summary of 41 Basic Knowledge of LTE
What Is The 5G Network Slicing?
